The Zero Trust Model: How to Get Started
Key Takeaways:
- The Zero Trust model is well worth the price and effort due to its long-term security advantages.
- This security framework requires all users, whether they are inside or outside the organization’s network, to be authenticated continuously.
- Implementing a Zero Trust security framework does not mean scrapping everything and starting from scratch, but there are factors that must be addressed.
- Ensuring that you’ve got executive buy-in on implementing Zero Trust is paramount.
What is Zero Trust All About?
According to the National Institute of Standards and Technology (NIST), Zero Trust is meant to “prevent unauthorized access to data and services coupled with making the access control enforcement as granular as possible.”
The National Security Telecommunications Advisory Committee (NSTAC) explains it as “a cybersecurity strategy premised on the idea that no user or asset is to be implicitly trusted.”
So, what does all this mean? Essentially, Zero Trust is asking you to approach your security strategy from the assumption that a breach has already occurred – or that one will occur – and therefore users, devices, applications, etc. should be continually verified. Zero Trust asks us to move away from location-centric cybersecurity models and to instead model strategies based on identity, context, and data, with ample security controls between users, systems, data, and assets. These security controls should be constantly updated and evolving.
This may sound like a lot of change, and frankly, it is. Zero Trust is not a matter of checking a box or changing a few security controls. Rather, it is an incremental process, a journey that you take across an extended period of time. Changing your approach to the Zero Trust model can incur some upfront costs, but the long-term security advantages it offers are well worth the price and effort.
Why Does Zero Trust Matter Today?
Per the Harvard Business Review, 2023 saw a 20% increase in data breaches compared to 2022, and the frequency of cyberattacks only continues to grow. Statista reports that 72% of businesses worldwide were affected by ransomware attacks in 2023. As attackers adopt more sophisticated methodology, utilizing new resources like artificial intelligence (AI), the cybersecurity landscape will continue to grow and evolve.
Additionally, businesses have changed. These days, organizations contend with more remote users and more data in the cloud. With that data spread across multiple clouds and third-party vendors (SaaS solutions), and with employees accessing data remotely, there’s more potential risk than ever before. Our traditional approach is not as effective as it once was – often, it’s not achieving what an organization needs from a business outcome perspective, or it’s putting up roadblocks thanks to legacy policies that haven’t been changed.
By adopting a Zero Trust approach to your cybersecurity, you’re asking for constant verification. This security framework requires all users, whether they are inside or outside the organization’s network, to be authenticated continuously. By taking this approach, you can help keep yourself alert and prepared for attempted attacks.
The Zero Trust Implementation Process
Implementing a Zero Trust security framework does not mean scrapping everything and starting from scratch. However, legacy systems that rely on implicit trust conflict with the core principle of Zero Trust and will need to be addressed.
In determining where to start, utilize a business perspective. Look at how your organization makes money. What’s your primary revenue stream, and what do your data security processes around that revenue stream look like now? What else could hurt your brand if it were breached or disrupted? Consider this from a regulatory and reputational perspective.
After considering these strategic initiatives, choose five or so to address and prepare protect surfaces for. A protect surface comprises critical data, assets, application, and services (DAAS), and is usually smaller than the whole attack surface, since it includes only critical assets.
Identify the DAAS needed to support the protect surface in question. What data needs to be protected? Which applications utilize sensitive information? Which assets are the most vulnerable, and which services can be exploited to disrupt normal operations? Identifying these protect surfaces is the process of aligning your cyber strategy to your business goals.
Once you define your protect surface, your next step is to determine your current state of maturity. We recommend performing your assessment against the Department of Defense Zero Trust Reference Architecture (DOD ZTRA) – this offers the most complete list of applicable controls for achieving Zero Trust maturity and the CISA Zero Trust Maturity Model v2, which can help in understanding the concepts of your Zero Trust maturity level.
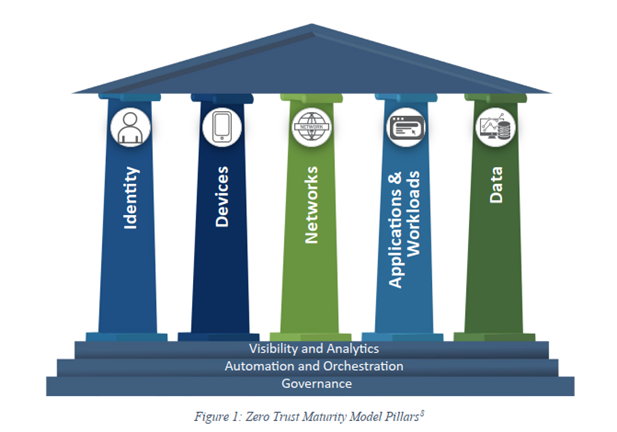
Once you’ve taken stock of your current state, compare it to where you want to be in terms of maturity at your target state. The gap between these two states will provide you with a list of tasks that need to be completed to bring your maturity up to par.
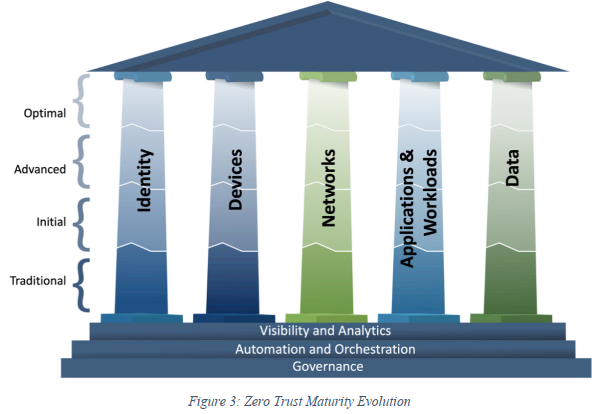
Currently, many organizations operate with a traditional security model that grants implicit trust to users and devices within their network perimeter, which can leave them vulnerable to sophisticated cyber threats. In contrast, the future state of maturity as defined by the Zero Trust model assumes no implicit trust, even for internal network traffic. To transition from the current state to the future state of maturity, organizations must undertake several tasks and activities.
To advance maturity towards this future state, organizations can perform activities such as conducting comprehensive risk assessments to identify vulnerabilities and prioritizing mitigation efforts. They can also implement robust identity and access management (IAM) solutions, deploy encryption for data protection, adopt a data-centric security approach, and integrate advanced analytics and threat intelligence for continuous monitoring and rapid response to security incidents. By addressing these tasks, organizations can evolve towards a mature Zero Trust security posture, significantly enhancing their defense mechanisms against evolving cyber threats.
These tasks can also be grouped together into initiatives that can cover multiple tasks. Prioritize each initiative based off estimated cost (consider initial cost and ongoing cost), estimated effort (consider initial staffing and ongoing staffing), and estimated benefits (consider alignment with your business goals and protect surface coverage).
Foster Executive Buy-In
Ensuring that you’ve got executive buy-in on implementing Zero Trust is paramount. This is not only because this is a lengthy, resource-intensive process, but also simply because Zero Trust is so important to your organization’s security. To those who balk at the resources required, stress that security improvements Zero Trust offers – avoiding a data breach is always worth investing time in. Explaining how your goals for Zero Trust dovetail into your business goals, as described above, will take you a long way in fostering buy-in.
Manage both your expectations and those of your board when it comes to timing – Zero Trust is not something that will be implemented in a few months, or even a year. It is a top-to-bottom review of your cybersecurity system that offers a more comprehensive approach to authentication and security, and so it will take time. Be patient with yourself and your progress. Additionally, your Zero Trust approach should always be evolving to meet your needs and to match the changing threat landscape.
Wolf & Company’s IT Advisory Team can help you with your Zero Trust strategy and implementation process. Whether it’s a maturity assessment, or implementation hurdles, we’re here to help. Reach out to our team today and let us know where you need assistance.