Written by: Matt Burns
Dangerous Defaults Part 2: Exchange Server Vulnerabilities
Key Takeaways:
- An Exchange server installed before June 2021 with an Active Directory schema that hasn’t been updated to remove the “msExchStorageGroup” schema class is vulnerable to exploitation.
- Similar to the “Add workstations to the domain” Group Policy setting, attackers can gain domain access.
- You can take steps to remediate this vulnerability.
In my last blog post, as part of our Dangerous Defaults series, I covered how default settings in an Active Directory (AD) domain can allow any domain user to add up to 10 machine accounts to the domain. I also covered how to remediate these issues. However, there is an edge case involving Exchange Servers, where even if you harden the “Add workstations to the domain” Group Policy setting, a user can still add a machine account to the domain.
When Can This Happen?
The edge case I am talking about is when an Exchange Server was installed in the Active Directory domain before June 29, 2021. The reason for this is that before this point when an Exchange Server was installed, it created the “msExchStorageGroup” schema class during installation. The issue with the “msExchStorageGroup” schema class is that it allows any domain user to create Active Directory objects such as a group, domain trust, or a machine account even if the “Add workstations to the domain” Group Policy setting has been properly hardened.
Microsoft released a security update for CVE-2021-34470, but the “msExchStorageGroup” schema class is not automatically removed after applying the update. So, what does this mean for you? Well, if you installed an Exchange Server before June 2021 and the Active Directory schema has not been manually updated to remove the vulnerable schema class, your environment is susceptible to this exploit.
How Can This Be Exploited?
This can be exploited in the same way as the “Add workstations to the domain” Group Policy setting. If the Lightweight Directory Access Protocol (LDAP) over TLS is enabled on the domain controller and hashes are relayed using the Impacket script ntlmrelayx, this attack is possible. Ntlmrelayx can relay hashed network credentials to the LDAPS service to create a machine account. If the user relayed does not have permission to add a machine account, ntlmrelayx will determine if the domain is vulnerable to CVE-2021-34470. If the schema class “msExchStorageGroup” is found, ntlmrelayx will exploit CVE-2021-34470 by adding a machine account to the domain:
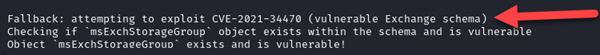
Figure 1 – Sample Impacket CVE-2021-34470
Similar to the “Add workstations to the domain” Group Policy setting, once the machine account is created, an attacker will have domain user access. Attackers can use this access to perform additional recon, escalate their privileges, deploy malware, etc. I have used this exact attack path on engagements in 2024 to achieve initial access to an Active Directory domain!
Remediation
Depending on the version of Exchange installed in the Active Directory environment, the remediation steps are slightly different. These various steps are outlined in the diagram in Figure 2 below. However, each step ensures that the security updates from July 2021 are installed, and the Active Directory schema has been updated to remove the vulnerable “msExchStorageGroup” class using the cumulative updates released by Microsoft in June 2021:
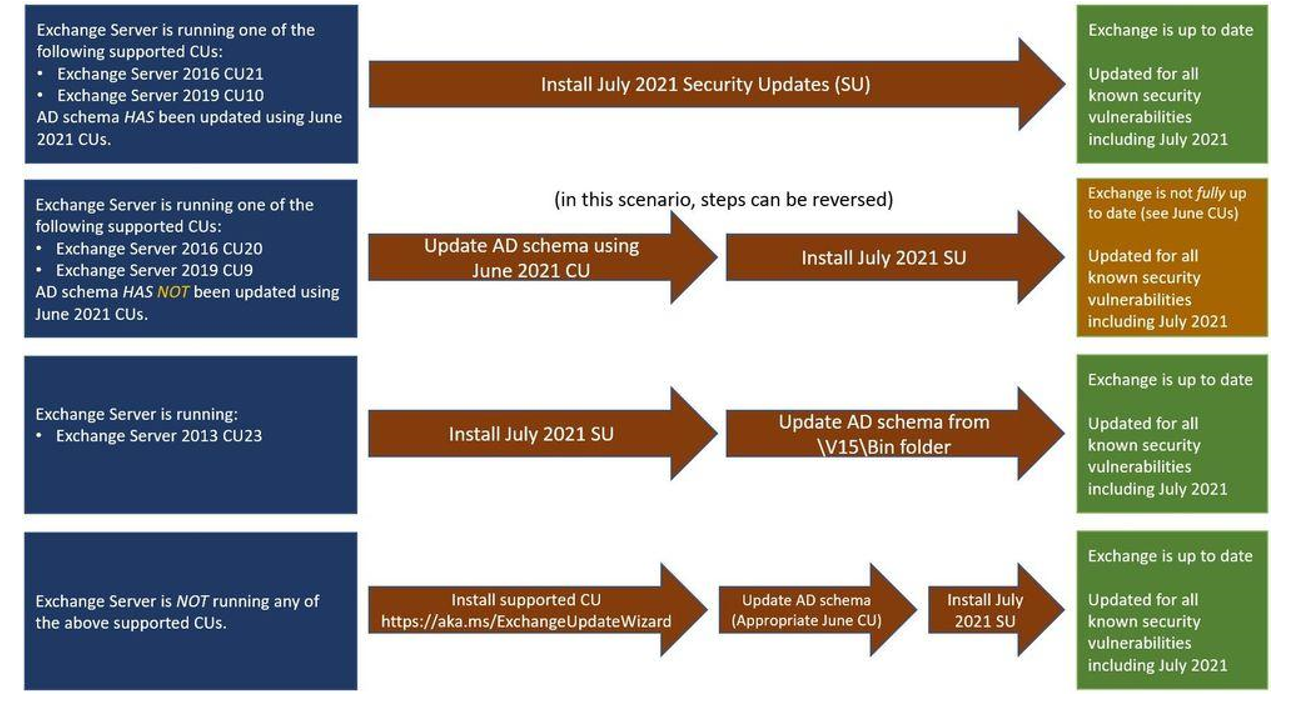
Figure 2 – CVE-2021-34470 Microsoft Remediation Steps
Microsoft released a full guide for how to remediate this issue for each case described in Figure 2 above. If you are worried about your Active Directory environment and want to know if you are vulnerable to CVE-2021-34470 or looking for reassurance about your security posture, check out our DenSecure service offerings.