Written by: Matthew Burns
In a previous blog post, I covered how an attacker with domain user access can utilize the Web Enrollment service on an Active Directory Certificate Services (AD CS) server to compromise a domain. In this blog post, I wanted to discuss how certificate template misconfigurations could also lead to a compromised domain by an attacker with domain user access.
What is a Certificate Template?
The role of an Active Directory Certificate Services server is to issue digital certificates throughout a domain. To accomplish this, the server will issue certificates based on the defined certificate templates. These templates are a group of settings that lay out how and why a certificate can be issued, as well as how it can be used. There are a number of default templates such as the “Machine” and “DomainController” templates, but administrators have the ability to configure their own. The creation of custom certificate templates without proper hardening can easily lead to a domain compromise.
What is One Way Certificate Templates Can be Abused?
There are many template misconfigurations discovered by Will Schroeder and others at SpecterOps that could allow an attacker with domain user access to fully compromise a domain. However, the template misconfiguration we see most often during our penetration testing, is known as escalation 1 or ESC1. This is when a low-privileged user (e.g., anyone in the Authenticated Users group) can request the certificate without a signature or approval, use the client authentication, and the requestor can specify the subjectAltName (SAN) for the certificate. A sample of a vulnerable template can be seen in Figure 1 below. The output in Figure 1 can be generated using the Certify/Certipy find command discussed in my first blog post about AD CS abuse.
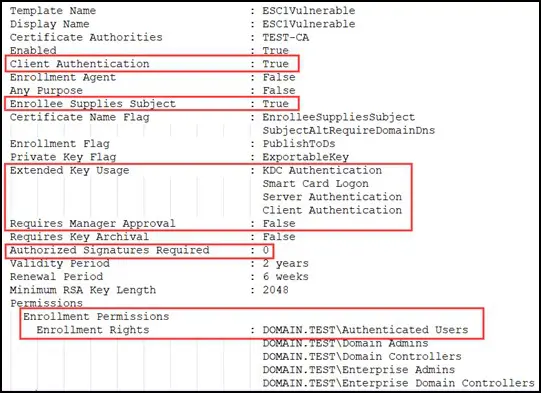
Figure 1 – ESC1 Vulnerable Template
The ability to specify the SAN for a certificate means that an attacker with a domain user account can request that certificate for any other user in the domain, including domain administrators. An attacker can perform this attack using a tool such as Certify/Certipy to generate a certificate for a domain admin user:

Figure 2 – Certipy Request
The certificate generated with Certify/Certipy can then be used to generate a Kerberos ticket granting ticket (TGT) for the user tied to the certificate. Now, this TGT can be used to get the new technology (NT) hash for the domain admin account. This means that an attacker with a domain admin certificate has access to the domain admin account since the NT hash is essentially the plaintext password in Active Directory environments. This is due to the fact that the NT hash can be used for pass-the-hash attacks.
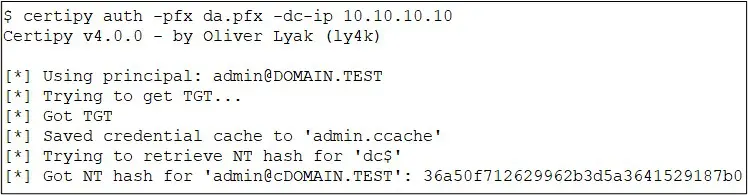
Figure 2 – Certipy Authentication
Remediation
There are multiple ways to remediate certificate templates vulnerable to ESC1. The easiest ways would be to either disable the ability for the certificate requestor to specify the SAN or disable the ability for low-level users to request the certificate. However, these changes could impact business depending on the need for the certificate template, so some additional hardening steps for administrators to consider include:
- Enabling manager approvals for the certificate templates that allow for authentication.
- Monitor the AD CS server(s) for certificate enrollments or requests.
- Segment the AD CS server(s) from standard user traffic.
Additional Considerations
In addition to ESC1 described above, there are many other certificate template misconfigurations that could lead to an attacker with domain user access compromising a domain. We could cover them all, but the SpecterOps blog post and white paper covers each escalation path in depth; we do recommend reviewing their post for a detailed description and remediation steps for each certificate template misconfiguration that could lead to domain compromise. We also recommend Administrators download the Certify/Certipy/PSPKIAudit and use one of these tools to audit their own AD CS server(s) and certificate templates for misconfigurations. If you have any questions about certificate template misconfigurations, a compromised domain, or more, our DenSecure team is here to assist.