Password theft is still the number one way we get inside client networks and access sensitive data. Hands
down, no question, period. And yes, it is in fact 2023.
However, it’s getting mildly (emphasis on mildly) more difficult to do. As clients implement the controls we recommend, such as Azure AD Password Protection for those with Azure/M365, the ability to acquire credentials quickly via password guessing is drastically reduced.
Lower, but not impossible, and here’s why: people will always be susceptible to social engineering attacks.
If I can’t get your password via password attacks, no problem. Instead, I’ll set up a chained social engineering attack that goes something like this:
- Gather information about your org that I can use to craft a phishing scenario
- Build a user list for my attack
- Craft a phishing email based on Step 1
- Set up phishing infrastructure that hides me behind legitimate services to bypass your spam/email security gateway
- Pair my email with secondary social engineering attacks, such as an MS Teams message, phone call, or another email leveraging Microsoft protocols that allow me to spoof internal users to validate the first two attacks
- Profit
Step 1 & Step 2: OSINT and User List Building
I will use LinkedIn primarily for this step. LinkedIn is a valuable tool not only for gathering info on the latest merger, a new employee welcome post, a deal that just closed, etc., but also for building a phishing victim list with tools like linkedin2username.
I will also use things like phonebook.cz, hunter.io, and ZoomInfo to gather more email addresses.
Finally, I will use a tool like TeamFiltration to not only validate that these addresses are good, but also pair that tool with statistically likely usernames to get even more valid addresses.
Step 3: Craft the Phish
This is the fun part and where we begin thinking about evading your defenses. Ever heard of MJML? Me either, until recently. Surely you have heard of ChatGPT by now, which is turning out to be a great tool for helping to craft phishing emails. Below, I asked ChatGPT to write me an email in MJML:
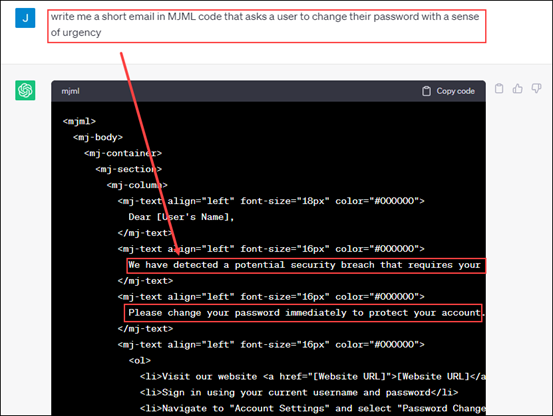
Now that I have this code, I can have another tool automagically turn this into HTML, which gives me a one-of-a-kind phishing email that your mail filter tools will have no reference for.
Step 4: Setting Up Sneaky Infrastructure
As I continue my evasive maneuvering, I set up my infrastructure. This is hosted in the cloud and leverages things like Content Delivery Networks (CDNs) to hide my credential theft pages behind Microsoft or other providers. I also send my phish through a trusted third party like MailGun, and set up tooling like Evilginx to perform Machine in the Middle (MitM) attacks that will pass off your valid credential information as well as MFA (multi-factor authentication) tokens (yeah, MFA isn’t your end-all control) back to me if you fall victim to my ruse.
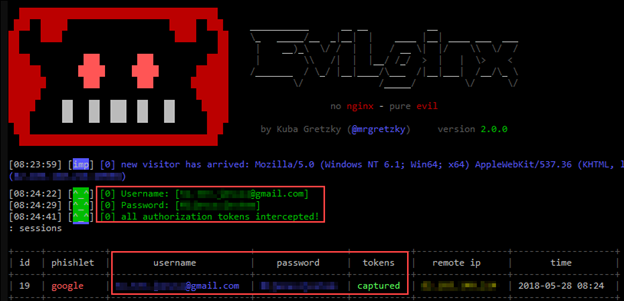
Step 5: The Chained Attack
If you are like most users, you have Microsoft 365, and therefore use MS Teams for chat with colleagues. Did you know that Microsoft, by DEFAULT, allows anyone outside your org to contact you? See where I am headed here?
Maybe after you get that email from me that says you need to change your password, I send you a message pretending to be an IT person and reference that email to ensure you received it and comply?
What if on top of that, I send another email leveraging Microsoft Direct Send that appears to come from a co- worker and is nearly impossible to distinguish? This email would also mention the validity of the original phish in some fashion, further legitimizing my evil plan.
Step 6: Profit
Now that I have convinced you to provide me your credentials, and ideally, your MFA token, I can access your inbox, send messages via MS Teams as you, find any passwords you’re storing in a file on OneDrive, download sensitive customer data, and so much more. Sometimes, this even results in command line access to the internal network.
What Can You Do?
So much! Just off the top of my head:
- Enforce passwords of 15 or more characters in length.
- Use a password strength security tool like Azure AD Password Protection.
- Roll out MFA and SSO to everything you can, ensuring your deployment is secure (no more “push” MFA).
- Ensure that inbound email can only be received through your mail security proxies like Mimecast, Proofpoint, etc.
- Disallow untrusted external orgs from being able to chat with your employees via MS Teams.
- Consider tuning the “paranoia” level (if possible) of your mail security proxy if too many attacks are making their way through.
With these steps, as well as what is hopefully a new insight into how attackers think, you will make it much harder for the real bad guys to cause your org pain in the future. Remember, it’s impossible to be 100% secure, but that doesn’t mean we shouldn’t always try to get there!





