Written by: Steve Nelson
Simple Mail Transfer Protocol (SMTP)? Good For You, Better For Me!
Key Takeaways:
- Simple Mail Transfer Protocol (SMTP) is pivotal for sending emails between clients and servers.
- Attackers can exploit SMTP vulnerabilities through spamming and spoofing.
- SMTP vulnerabilities enable attackers to use tools like Telnet or Netcat to send emails, probe for open relays, and verify email addresses for targeted attacks or spam.
- Implementing measures like access restrictions, encryption, proper configuration, vendor discussions, and email authentication can reduce vulnerabilities.
What is SMTP?
SMTP, also known as the Simple Mail Transfer Protocol, is the backbone of email exchanges on the Internet, demanding our attention. It’s not just a tool for system administrators and developers but the key to understanding potential vulnerabilities that attackers can exploit. Let’s delve into the world of SMTP and its significance in digital communication security.
You may be thinking, “Hey! Wait a second! I just mitigated Direct Send! How could this be affecting me?”
At its core, SMTP is the messenger that sends messages from an email client to an email server or between servers. But it doesn’t work alone. It’s a team player that closely works with other protocols like Internet Message Access Protocol (IMAP) or Post Office Protocol (POP), which manage email retrieval and storage on the receiving end. Despite its widespread use and essential role in digital communication, the Simple Mail Transfer Protocol is not without its flaws, particularly concerning security:
- Spamming: SMTP servers can be targeted to send out spam emails. Attackers can exploit open SMTP relays (servers configured to allow third-party emails through without authentication) to send bulk emails, often for phishing or spreading malware.
- Spoofing: Email spoofing involves forging the sender’s address on an email to appear as if it was sent by someone else, typically to mislead the recipient about the message’s origin. SMTP does not inherently authenticate outgoing messages, making it possible for attackers to spoof email addresses.
How Attackers Can Exploit SMTP
One lesser-known yet critical, and simple, vulnerability involves direct connection to SMTP servers. Here’s how it can be exploited:
- Direct Access: Similar to Direct Send communicating with a smart host, attackers can connect directly to exposed SMTP servers using tools like Telnet or Netcat. Using crafted SMTP commands allows them to send emails with minimal restriction. This method can also probe for open relays or vulnerable servers that do not require authentication.
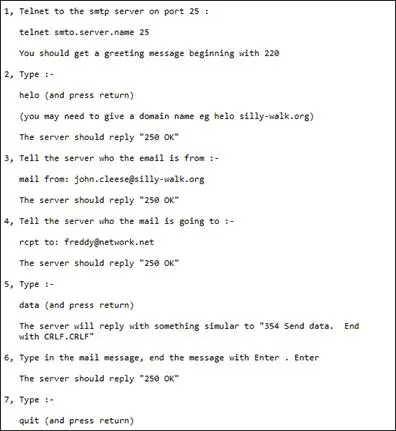
Figure 1 – SMTP Commands
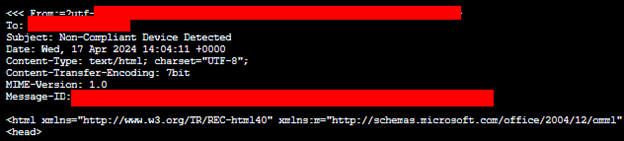
Figure 2 – Example of Espoofer Tool
- Directory Harvest Attack (DHA): By directly connecting to an SMTP server, an attacker can attempt to verify the existence of specific email addresses at a domain. This is typically done by issuing commands to send emails to various addresses and observing the responses. Successful guesses can be used for more targeted attacks or spam.
Best Practices to Mitigate SMTP Risks
To secure SMTP servers and mitigate these risks, administrators should consider several best practices:
- Restrict SMTP Access: Limit who can send emails through the server. Requiring authentication helps prevent unauthorized use.
- Implement Encryption: Use TLS to secure all SMTP connections, ensuring that emails cannot be easily intercepted or altered in transit.
- Configure Properly: Implement rate limiting to reduce the impact of potential DDoS attacks.
- Vendor Discussion: Talk to your mail gateway vendor to discuss what is being done to protect against spoofing. For example, check the “From” header in SMTP to see if it is legitimate.
- Use Email Authentication Methods: Implement SPF, DKIM, and DMARC to help detect forging sender addresses, thereby preventing spoofing and enhancing email integrity.
For those interested in exploring these vulnerabilities further, tools like “espoofer” on GitHub provide practical insights into exploiting various aspects of SMTP, specifically email spoofing techniques. This tool provides multiple ways to check for vulnerabilities in your company’s mail gateway. Credit for this tool goes to Jianjun Chen.
SMTP is crucial in our daily communications and presents numerous security challenges. By understanding these potential risks and implementing robust security measures, organizations can significantly reduce their vulnerability to attacks exploiting SMTP weaknesses.
Connect with our DenSecure team today to learn how we can ensure you don’t fall victim to SMTP attacks.