Written by: Richard Rocchio
There were approximately 3.8 million Bank Secrecy Act (BSA) reports filed related to $556 billion worth of suspicious activity in 2021. The main drivers of that dollar amount were general fraud, false records, and identity theft. While this data is from 2021, there is no doubt that these trends have only grown as society has returned to post-COVID normalcy.
Summary of Key Findings
Most attackers have impersonated others to defraud victims. Of approximately 3.8 million total BSA reports, 69% included attackers impersonating others to defraud victims. The other two most popular reports included attackers using compromised credentials (18%) and attackers exploiting insufficient verification processes (13%).
FinCEN used the NIST Digital Identity Guidelines to determine the steps to confirm identity. The process to confirm identity includes three parts: validation, verification, and authentication. Essentially, a user validates that their identity exists and is unique, they then verify that identity with a driver’s license, passport, or a form of biometrics. Once the identity is verified, a user will attempt to authenticate if they have the necessary tools. Those tools are general knowledge (something you know), biometrics (something you are), or some sort of token (something you have). If any of these steps are insufficiently implemented, such as multi-factor authentication not being enabled, an attacker will have an increased likelihood of being able to gain access to a user’s account.
The ways the report finds that attackers are exploiting this simple three-step process is by Impersonation, Circumvention, and Compromise. By pretending to be a valid user, the attacker does not need to find a more technical way in (i.e., hacking).
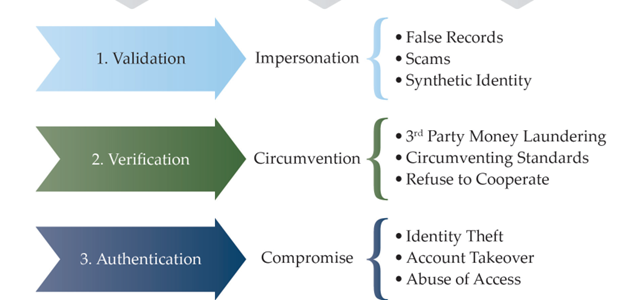
Courtesy of FinCEN
Social engineering is an especially large threat to each of these steps to confirm identity. For validation, there is very little complexity required by an attacker. By scanning social media sites and other publicly available data, or even shoulder surfing, an attacker can learn quite a bit about a potential victim.
From there, attackers are easily able to impersonate a victim and may be able to circumvent the verification controls that are not implemented up to industry best practices. Without multi-factor authentication, an attacker may be able to guess a password if the controls are insufficient. An attacker can also attempt to trick a victim into giving them their password or One-Time Passcode (OTP) with a fabricated scenario or ruse. Having successfully gained access, the possibilities are wide-ranging in what an attacker can do. They can complete unauthorized transactions, access personal information, or commit identity theft.
The report also warns that the rapid evolution of Artificial Intelligence (AI) may further enable bad actors to exploit outdated identity processes to drive fraud, money laundering, and other cybercrimes. For example, a common tell on phishing messages is poor grammar and spelling. With the advent of AI, perfectly written sentences can be generated in a matter of seconds.
Actions an attacker can complete after successfully impersonating someone can include but are not limited to:
- Opening fraudulent bank accounts
- Receiving government benefits
- Applying for lines of credit
- Depositing counterfeit checks
- Perpetrating online scams playing on a person’s emotions (romance scans, person-in-need, etc.)
The National Money Laundering Risk Assessment also found that fraud is the largest form of suspicious activity year over year. Fraud or “general fraud” can be described as check fraud, debit/credit card fraud, and unauthorized transactions. Included in credit card fraud are bust-out schemes. This is defined as an attacker using false information to open a credit card and then quickly max the card out.
As directed by the Anti-Money Laundering (AML) Act of 2020, FinCEN has coordinated with the private and public sectors to define the risks and challenges of emerging technologies used by financial institutions. The group has identified digital identities, AI, and Privacy-Enhancing Technologies (PET) as tools that may help customers identify exploitation and suspicious activity before the Bank’s AML system can.
Periodic reviews of applications and asset management can ensure authentication controls are in line with the best practices and regulatory requirements. Hands-on social engineering testing can test the “human firewall” to assess the potential exposure of gaps in the verification process. Social engineering and evaluations of the customer-facing controls can ensure that validation controls are adequately implemented based on the institution’s risk profile.
Many of the attack vectors discussed in this report are not new and are rather exploiting chips in an institution’s foundation that develop over time (i.e., missing updates, patches, and periodic reviews of systems). Wolf & Company’s experience and expertise can help financial institutions address this increasingly risky space through evaluations of the current state of the fraud landscape, recommendations for the future, and insights on new technologies and best practices. If you’re looking for assistance with preventing fraud at your institution, reach out to Wolf & Company today.